Web-site Protection
THIS ARTICLE IS NOT UPDATED. WE ARE ON THE INTERCOM NOW!
http://help-center.peerclick.com/en
JOIN US THERE AND WATCH ALL UPDATED PEERCLICK GUIDES!
Hello, this manual will show how to properly configure the Cloaking, as an example we will use Facebook.
First of all we need a Basic+ tariff and higher with cloaking, Basic+ costs $ 99 per a month.
Then we go to our host or server and add there our white landing page, so that it shows up when the bots / moderator of the network that you have chosen for cloaking transfer to your site.
What are the requirements for the domain?
- A domain must have an HTTPS protocol (ssl).
- The domain where will be a "white" site for bots and spies should not have been advertised earlier.
- The domain where the main site will be (for ordinary users) - can be any.
For example, We take the domain: example.com and insert it into the root of the landing for dating.
Then, we go to the PEERCLICK panel and start setting up the cloaking.
Go to the Sources and create a new source that you need, in our case it will be FACEBOOK
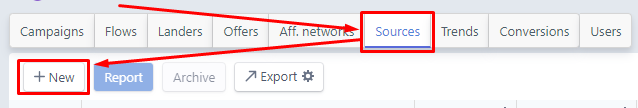
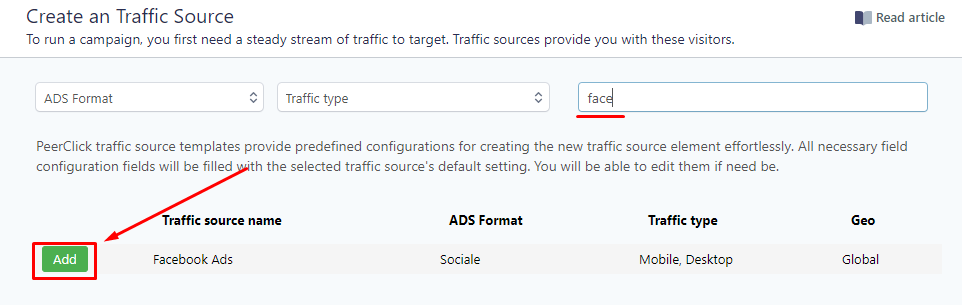
Enter FACEBOOK in the search and click the Add button and save.
Then, we go to the Campaigns and create a new campaign and choose the type of campaign Web-site Protection
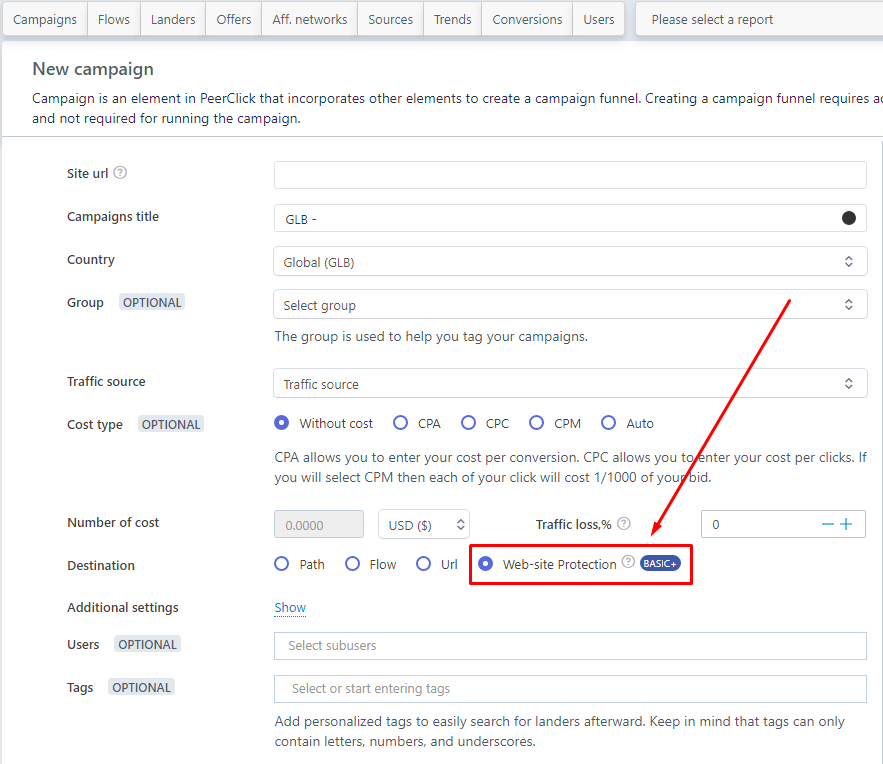
Choose and go to configure
-
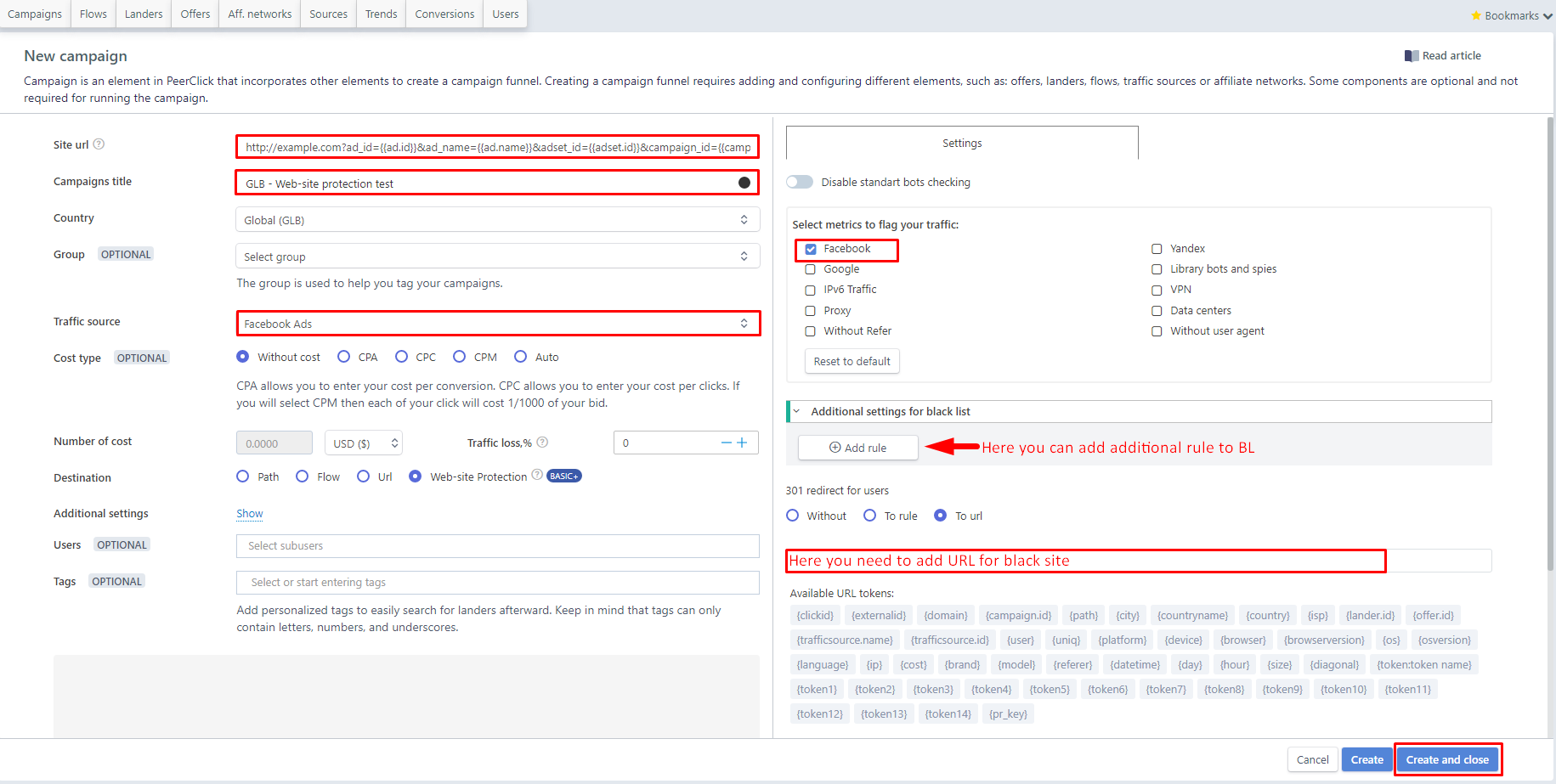
Add a domain, in our case it will be: https://example.com
-
Write any campaign name.
-
Next, choose the country we plan to pour the traffic on, in our case it’s Global.
PeerClick Info
In this case, the choice of the country is only informative and does not affect the work.
- Choose the source of traffic that we created. It’s Facebook.
PeerClick Info
Such sources as: Vkontakte, MailTarget, Odnoklassniki and others smaller ones are collected in the filter Library bots and spies
-
Destination - choose Web-site Protection
-
Then, we go to the filters and choose Facebook. Make sure to configure additional rules. For example, if traffic is to USA, then all other countries should be bots. You also need to select the type of device (for example, only the desktop). You can add more VPN / PROXY traffic filtering.
-
Next, choose 301 redirect to url (link taken from the Partner Program)
-
Then click Save and close
It’s almost ready, but it’s not all. Edit the created campaign and select the tab which you see on the screenshot, "PHP script"
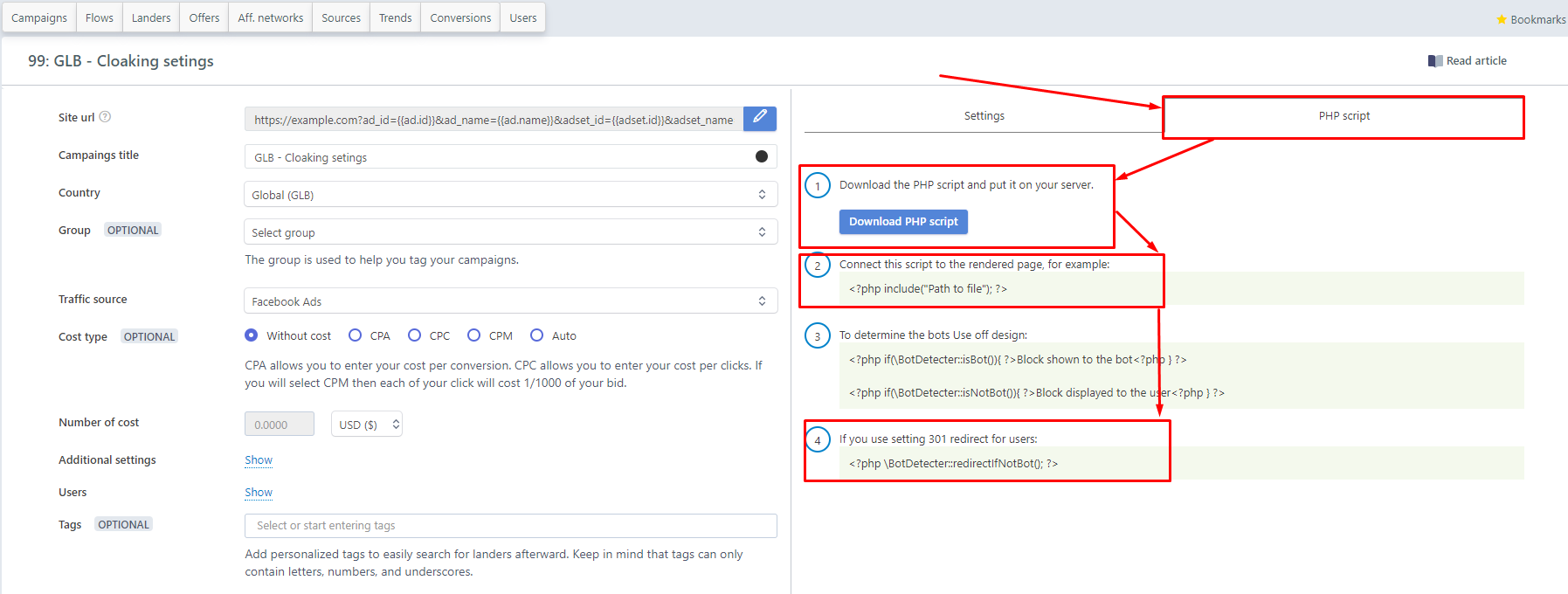
Download the script on your computer and then take this file to the hosting and connect it on our site.
We see in the archive a script with this name: 146-15FeYt, for convenience we change the name, for example, to playok or whatever you come up with. After that, we upload this file to your hosting into the root.
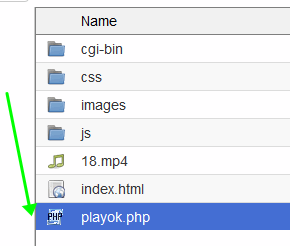
Next, go to the main page of site into the file index.html and write these 2 lines at the top:
And save the changes. After that, change the file format from index.html to index.php, otherwise our cloaking won’t be connected as it should be.
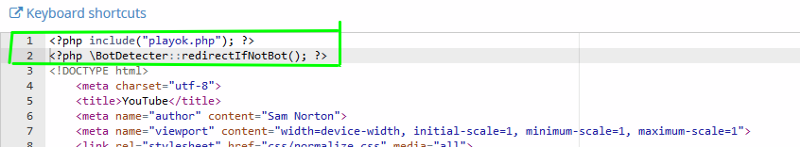
If everything is done correctly, your hosting will look like this:
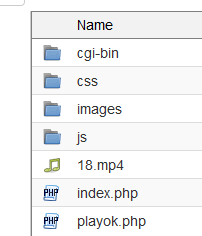
Where index.php is the home page of the land, playok.php is the cloaking connection file.
Check that your PHP is at least 7.0 version otherwise it will not work.
Let’s summarise final steps are left:
-
You need to place your “white” site on your domain, which hasn’t been advertised earlier in Adwords/Facebook and etc. (we have used this one: https://example.com )
-
Set up advertising by specifying a “white” site and wait for moderation. Don’t forget to pause a cloaking before these actions.
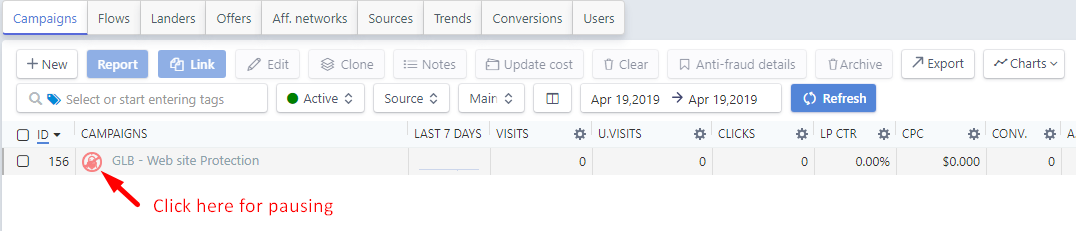
- After moderation, turn on cloaking (put on the same button when it becomes green).
That’s all. Bots and spies will see “white” site and users will see any site, that you have specified. As a result, we got a ready-made cloaking for draining the FACEBOOK traffic.
Also you can watch our video with Cloaking manual:
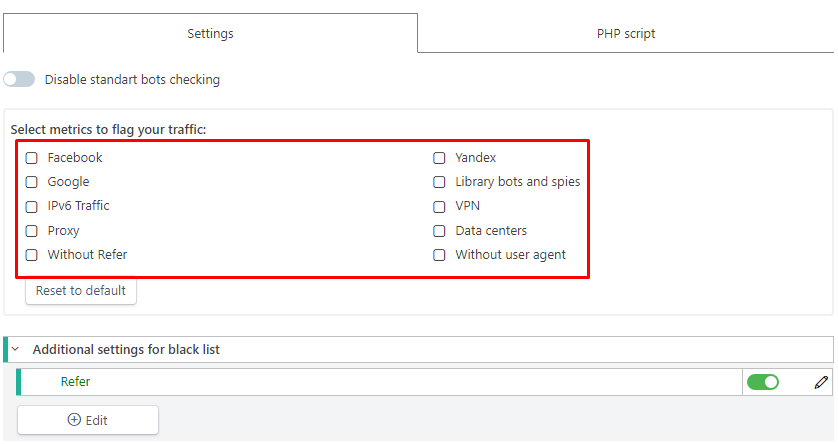
More details on the filters that can be applied to Web-site Protection
Filters Web-site Protection
Facebook, Google, Yandex - databases of bots and moderators of the most popular traffic sources.
Library bots and spies - The rest of the traffic sources are included in this filter (Vkontakte, Mail Target, Odnoklassniki, etc.)
IPv6 Traffic - traffic using the Internet Protocol version 6. In the CIS, the technology is not yet widespread. Basically it is used by large campaigns.
VPN - traffic using an encrypted VPN connection.
Proxy - traffic using a proxy connection.
Data centers are data storage and processing centers, traffic from such IPs most likely indicates bots traffic.
Without referer - traffic received without URL source data of the request. Most likely it indicates a click not on the ad, but on the direct link.
Without user agent - traffic received without data from the client application. It is also most likely indicative of traffic belonging to bots.
Based on tests of different filters for your traffic, you identify the most productive configuration for you. Note that the use of all filters will most reliably protect your traffic, however this may reduce its number as some sites specifically overwrite the referer or employees of large companies can use working PCs and their IP addresses will be related to the data centers that you disabled by applying the filter data center .
PeerClick provides a productive tool in the hands of an afilliate marketer, on the basis of which you can create a reliable protection for your site.
Updated over 5 years ago
